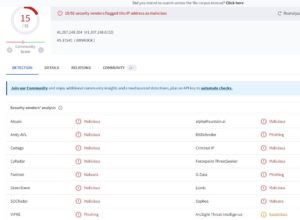
WatchDogCyberDefense has been emailing the Network Owners/Admin of the listed IP address for over 2 years. The attacks keep on coming without any resolution from the Hosted Providers.
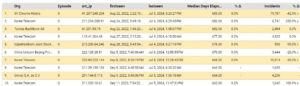
This is also an indicator of POOR network/security admin performance. No wonder the IP of SV Chrome Hotels is also listed by Virustotal as “malicious”. Our guess is that this network is totally compromised by hackers and the management has no idea that their network/IT guys are complacent about it.