A common question in cybersecurity circles is: How can business email accounts be compromised even when the user never clicks a phishing link or downloads malware?
To explore this, we analyzed 50,000 email addresses from across Asia Pacific, New Zealand, and Australia. Each address was checked against HaveIBeenPwned.com to determine whether it had been exposed, and if so, through what type of incident. We also reviewed academic research, including “Who is Targeting You? A Multi-dimensional Analysis of Account Hijacking” by Kurt Thomas and colleagues from Google, UC Berkeley, and ICSI. Their 2015 study found that the leading causes of business email compromise (BEC) were keyloggers, followed by phishing, and then third-party breaches.
Our findings, however, tell a different story. After cleaning and analyzing the dataset, we discovered that the number one source of email account compromise today is not keyloggers or infostealers—it’s third-party data leaks.
This insight carries significant implications for organizations. If corporate email addresses are being exposed primarily through external breaches, then usage policies, vendor risk management, and compliance monitoring become just as critical as user awareness training and malware defense.
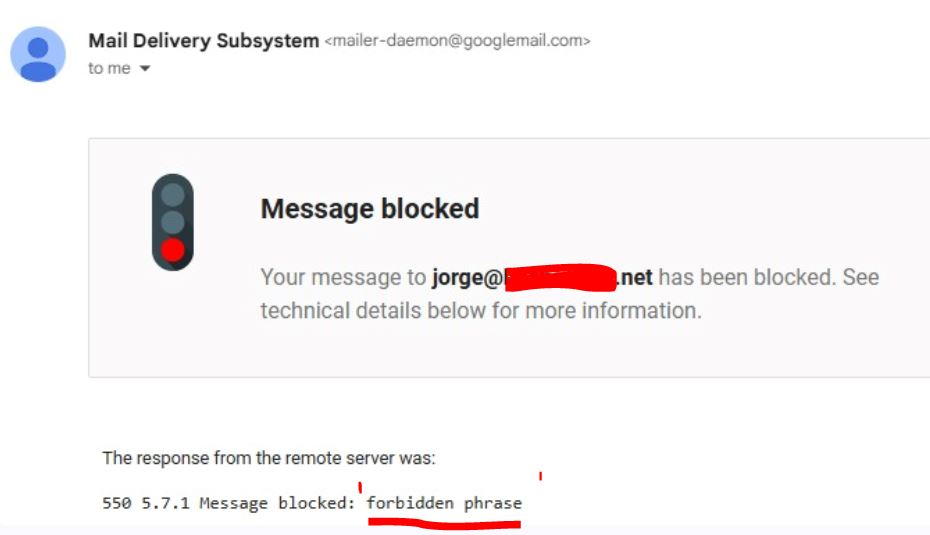
One tactic to enforce corporate policy of not allowing corporate email to be used in registering for 3rd party sites is to block emails containing certain keywords: “confirm your account”, “Verify your email”, “complete your registration”, “Welcome to”, “Activate your account” etc. Users will get a “message blocked” error like this: