When people think about cyberattacks, they often picture hackers breaking into computers using secret codes or fancy tools. That’s one kind of threat called a technical intrusion. But there’s another, sneakier kind that doesn’t rely on technology at all. It’s called social engineering, and it targets people instead of machines.
Both can cause huge damage. But the good news is, your organization can defend against both with the right mix of continuous software updates and continuous cyber education.
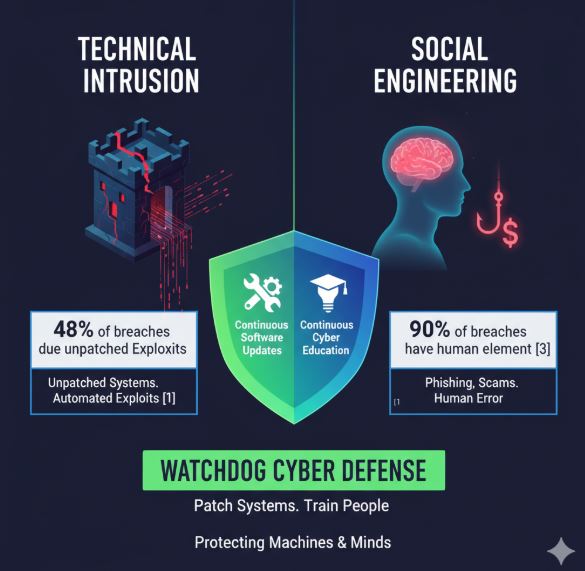
1. Technical Intrusion: When Machines Attack
Technical intrusions are what most people imagine when they hear hacking. Attackers look for weaknesses in your systems like outdated software, unpatched servers, or misconfigured firewalls and sneak in through those gaps.
Every time your software or operating system updates, it fixes known security flaws. But if your company delays updates, those flaws stay open like unlocked doors in your network. Hackers scan the internet every day, searching for systems that haven’t been updated. Once they find one, they can steal data, install ransomware, or take control of devices.
Indeed, a significant portion of breaches are due to unpatched vulnerabilities. According to a 2022 report by the Ponemon Institute, 48% of organizations experienced a data breach caused by an unpatched vulnerability within the past two years. This highlights the critical importance of timely patching [1]. Furthermore, the CISA (Cybersecurity and Infrastructure Security Agency) frequently releases alerts about vulnerabilities being actively exploited in the wild, often emphasizing that these exploits target known, unpatched flaws [2].
That’s why continuous software upgrades are the foundation of strong cybersecurity. It’s not a one-and-done thing. Just like brushing your teeth daily instead of once a year, you need regular updates and patches to stay safe.
Watchdog Cyber Defense helps companies monitor these updates. Our system identifies outdated software and vulnerabilities so your IT team can patch them before criminals do.
2. Social Engineering: When People Are the Target
Even the best technology can’t stop someone from being tricked. Social engineering attacks, like phishing emails, fake invoices, or voice scams, aim to manipulate people into giving up passwords, clicking malicious links, or sending money.
According to studies, over 70% of successful data breaches start with a social engineering attack. Specifically, the Verizon Data Breach Investigations Report (DBIR) consistently ranks social engineering, particularly phishing, as a top threat vector. Their 2023 report found that 90% of all data breaches had a human element involved, with phishing being present in 36% of breaches. [3]. Another study by Proofpoint revealed that 91% of successful cyberattacks begin with a spear-phishing email. [4]. Why? Because employees are busy, distracted, or unaware that the email they just opened wasn’t really from their boss or bank.
Technology can block some of these attempts, but people need training to recognize them. That’s where continuous cyber education comes in.
3. Training Your Human Firewall
Your employees are your first and last line of defense. Just like software needs regular updates, your staff needs regular security refreshers. A one-time seminar or annual lecture isn’t enough. Cyber threats evolve fast so should your team.
Research supports the effectiveness of continuous training. A study by the SANS Institute indicated that organizations with ongoing security awareness programs reported 50% fewer successful phishing attacks compared to those with infrequent or no training [5]. Another report by Cofense found that regular phishing simulations can reduce an organization’s click-through rate on malicious emails by up to 80% [6].
Watchdog Cyber Defense makes this easy. We provide micro-lessons, short 3-5 minute learning modules that teach key cybersecurity habits. Each lesson covers a simple, real-world topic like spotting a phishing email or securing your Wi-Fi. These micro-lessons fit right into the workday and keep awareness high all year round.
We also run phishing simulations safe, realistic fake attacks to test and improve your employees’ alertness. It’s like a fire drill for cybersecurity. Employees learn by doing, and managers can see where extra training is needed.
4. Staying Safe: A Continuous Process
Cybersecurity isn’t a one-time project; it’s an ongoing process. Software needs continuous updates to defend against technical intrusions. People need continuous education to defend against social engineering.
With Watchdog Cyber Defense, your organization gets both the tools to patch your systems, and the training to patch your people. Together, they form the strongest protection against the two biggest types of cyber threats today.
Let’s have a quick chat about how managers can do to keep their business system safe and protect their operation. Email us at roger.do@watchdogcyberdefense.com
References:
[1] Ponemon Institute. (2022). The Cost of a Data Breach Report. https://www.ibm.com/reports/data-breach
[2] Cybersecurity and Infrastructure Security Agency (CISA). (Ongoing). Known Exploited Vulnerabilities Catalog.
[3] Verizon. (2023). 2023 Data Breach Investigations Report (DBIR).
[4] Proofpoint. (Ongoing). Human Factor Report.
[5] SANS Institute. (Various reports and whitepapers on security awareness).
[6] Cofense Intelligence-driven Phishing Defense.
