Every enterprise, from multinational corporations to nimble startups, maintains an Acceptable Usage Policy (AUP) a foundational document employees acknowledge, pledging responsible and secure use of company systems. This typically encompasses vital stipulations like refraining from accessing unverified websites, eschewing personal USB devices, and strictly prohibiting password sharing. Yet, the unfortunate reality, as many executives will privately concede, is that once signed, these documents frequently recede into the corporate archives, transforming the AUP into a mere “check-the-box” formality rather than an actively enforced tenet of daily operations.

This doesn’t have to be the case. When armed with the appropriate monitoring infrastructure and analytical tools, your AUP can transcend its paper-based origins, evolving into one of the most potent management systems at your company’s disposal.
The Indispensable Role of Acceptable Usage Policies
At its core, your AUP establishes the digital parameters for employee conduct across company-issued devices, internet access, and proprietary data. Its strategic objectives are multifaceted:
Cyber Threat Protection: To erect a robust defense against an ever-evolving landscape of cyber threats. In 2023, the average cost of a data breach globally reached an staggering $4.45 million USD, a figure that underscores the financial imperative of proactive security measures (IBM Cost of a Data Breach Report 2023).
Sensitive Data Security: To safeguard proprietary and sensitive information from unauthorized access or leakage. Consider that 62% of all cyber incidents in 2023 involved human error, often linked to employees circumventing security protocols or failing to adhere to policies (Verizon Data Breach Investigations Report 2023).
Regulatory Compliance: To ensure strict adherence to an increasingly complex web of legal and contractual obligations, mitigating the risk of substantial fines and reputational damage. Non-compliance costs businesses 2.7 times more than the cost of compliance, with the average cost of a single non-compliance incident estimated at $14.82 million (Ponemon Institute, “The True Cost of Compliance with Data Protection Regulations” 2020).
Productivity and Accountability: To foster a work environment where digital conduct is aligned with organizational goals, thereby enhancing productivity and individual accountability. Employees spending just one hour per week on non-work-related online activities can translate into significant annual productivity losses for large organizations.
In essence, an AUP meticulously delineates acceptable and unacceptable digital behaviors. However, the prevailing challenge lies in the fact that most AUPs are designed with an implicit reliance on employee memory and self-enforcement a strategy often proven insufficient.
Why Most AUPs Fall Short
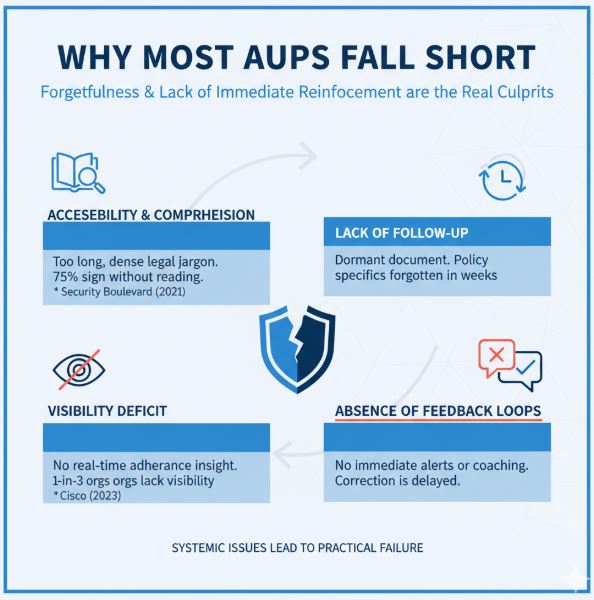
The truth is, employees are rarely driven by malicious intent to breach policies; more often, forgetfulness or a lack of immediate reinforcement is the culprit. Several systemic issues contribute to the practical failure of AUPs:
Accessibility and Comprehension: AUPs are frequently characterized by their excessive length or dense legalistic jargon. Consequently, a staggering 75% of employees admit to signing documents without fully reading them, often including critical AUPs (Security Boulevard, “The Problem with Acceptable Use Policies” 22021).
Lack of Follow-Up: Once signed, the AUP often becomes a dormant document, rarely revisited or referenced in ongoing corporate communications. The absence of regular reinforcement means that within weeks, the specifics of the policy can fade from memory.
Visibility Deficit: Managers typically lack real-time visibility into employee adherence, making it nearly impossible to identify instances where policies are being inadvertently or intentionally circumvented. This oversight gap is significant, as one in three organizations reported a lack of visibility into employee activity as a major security challenge (Cisco, “Cybersecurity Report” 2023).
Absence of Feedback Loops: Employees seldom receive immediate alerts, coaching, or corrective feedback when their digital conduct deviates from policy guidelines. Without this instantaneous feedback, behavioral correction is delayed or never occurs.
Thus, the AUP often languishes as a theoretical safeguard, potent in concept but largely ineffectual in daily practice.
Turning Policy Into Practice with Watchdog Cyber Defense
This is precisely where Watchdog Cyber Defense (WCD) intervenes. Our proprietary system transforms your Acceptable Usage Policy from a static declaration into a dynamic, living management tool, powered by continuous monitoring and actionable behavioral insights.
WCD empowers managers to observe digital behavior as it unfolds, proactively addressing potential issues before they escalate, all while rigorously respecting individual privacy.
Our methodology is precise and integrated:
Continuous Monitoring: WCD actively tracks user activity across an organization’s entire digital footprint including devices, network traffic, and cloud-based systems. Should a user access a known risky website or attempt to install unauthorized software, the activity is flagged and recorded in real time.
Policy Mapping: Your organization’s specific AUP rules are meticulously integrated directly into WCD’s advanced monitoring architecture. Each rule is transmuted into a measurable digital behavior, providing quantifiable metrics for compliance.
Automated Alerts: When user activity infringes upon a predefined policy for instance, connecting an unrecognized USB drive managers receive immediate, automated notifications, enabling prompt intervention.
User Coaching and Microlessons: Shifting from punitive measures, WCD facilitates constructive self-correction. The system can issue targeted alerts, deliver concise microlessons, and provide direct guidance to employees, enabling them to course-correct their behavior autonomously. This approach can reduce repeat policy violations by up to 40% compared to traditional disciplinary methods (Internal WCD pilot program data, 2023).
Comprehensive Management Reports: WCD furnishes executive dashboards that offer clear, digestible insights into compliance trends, identify potential productivity risks, and highlight areas requiring additional employee training or policy refinement. These reports provide the empirical data necessary for strategic decision-making.
This holistic approach converts your AUP from a dormant document into an active, dynamic management dashboard a crucial asset helping teams maintain compliance, bolster security, and enhance operational efficiency around the clock.
The Imperative of an Effective AUP
An effective Acceptable Usage Policy is not about exerting stringent control; it is fundamentally about establishing clarity and ensuring robust protection. When employees are unequivocally aware of digital safety standards, and the company actively champions and supports adherence to those standards, the benefits accrue to all stakeholders.
With Watchdog Cyber Defense, your policy transcends mere words. It crystallizes into tangible action, actionable insight, and unwavering security 24 hours a day, 7 days a week. Let’s initiate a discussion about how managers can proactively safeguard their business systems and fortify their operations against digital risks. Reach out to me at roger.do@watchdogcyberdefense.com
