According to NixCraft, a credible source in the cybersecurity community, a state-sponsored hacking group infiltrated F5 Inc. the global provider of application delivery and network security solutions in late 2023.
The attackers reportedly remained undetected inside F5’s internal systems until August 2024, highlighting significant concerns over supply chain compromise, zero-day exploitation, and persistent threat operations targeting critical infrastructure vendors.
Exposure Across Asia
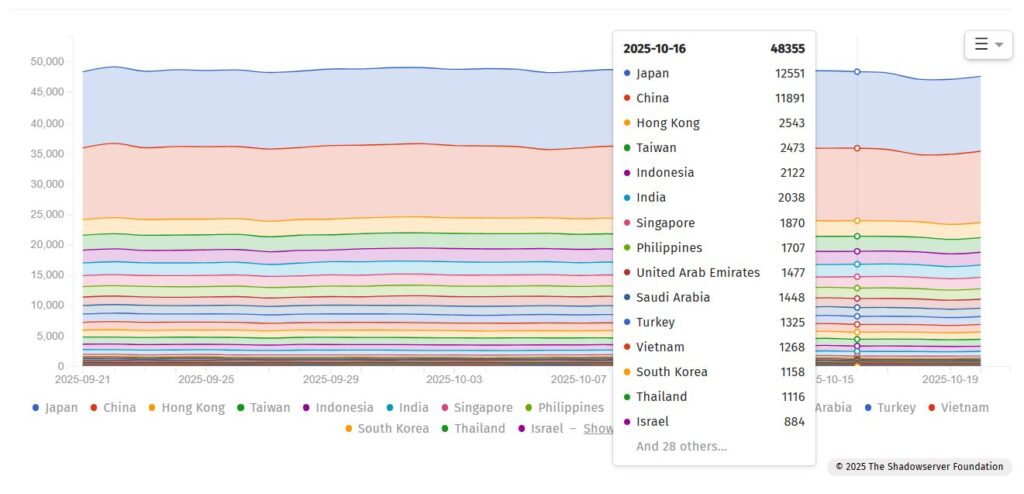
A review of the ShadowServer Foundation’s dashboard reveals the scale of F5 device exposures across Asia, suggesting that hundreds of publicly reachable systems may still be at risk. These exposed assets could potentially be leveraged by advanced persistent threat (APT) actors to gain deeper access into enterprise networks. Japan and China lead the pack in terms of most number of exposed F5 devices for the period ended Oct 22, 2025.
Why It Matters
This breach underscores:
- The increasing sophistication of nation-state cyber operations.
- The importance of continuous monitoring, patch management, and threat intelligence sharing.
- The risks associated with third-party security providers that form part of the global cybersecurity supply chain.
- Experts warn that even companies specializing in defense technologies are not immune from covert intrusion campaigns.