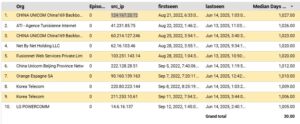
WatchdogCyberdefense.com dataset shows that the Top 10 IPs have been seen attacking our clients for the LONGEST time:
In contrast to one-off or bursty traffic patterns, sustained attacks often involve repeated actions over an extended period, aiming to overwhelm, infiltrate, or persist within a target system.
Persistence Signals Intent
Most legitimate users, bots, and even misconfigured scripts generate short-lived, predictable interactions. Malicious actors, however, often linger:
- Brute force attempts: Can last minutes or hours, trying thousands of password combinations.
- Data exfiltration: Takes time, especially when attackers throttle traffic to avoid detection.
- C2 communications: Maintain steady, low-volume connections over days or weeks.
In each case, the duration reflects persistence, and persistence reflects intent. To counter check, we queried app.crowdsec.net to see how many of these top 10 IPs are actually Malicious. The results shows that 100% of indeed, malicous. Example: 14.6.16.137: