We’re actively sending abuse alert emails to network owners, alerting them to potential compromises on their servers. Recently, several TOR operators (middle, guard, and exit nodes) have reached out, reporting that their IPs were spoofed. While these claims have validity, we’d like to highlight that a significant amount of the TCP port 22 traffic we observed involved genuine established sessions. Some MIDDLE node operators were even able to confirm compromises on their systems and have since taken steps to clean them up.
This experience got us thinking about the need for a swift way to identify spoofed IPs involved in attacks that create substantial backscatter traffic, potentially resulting in DDoS attacks on the actual IP. To address this, we’ve begun developing a methodology to help ISPs pinpoint the real source of these spoofed IPs.
Stay tuned as we make progress on this approach to enhance network security across the board!
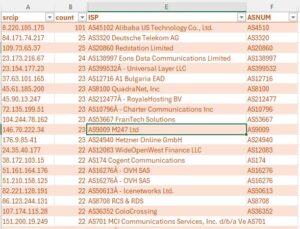
Here is a partial list of such spoofed IPs uncovered using the seminal methodology: